Trusted By
.png)










.png)










Meet Your Agentic Security Architect
Assigned to every single team, developer, sprint, feature…
Finally, Preemptive Security at scale
Minutes to Deploy + Immediate Time to Value
(aka your security team's new best friend)


Discover
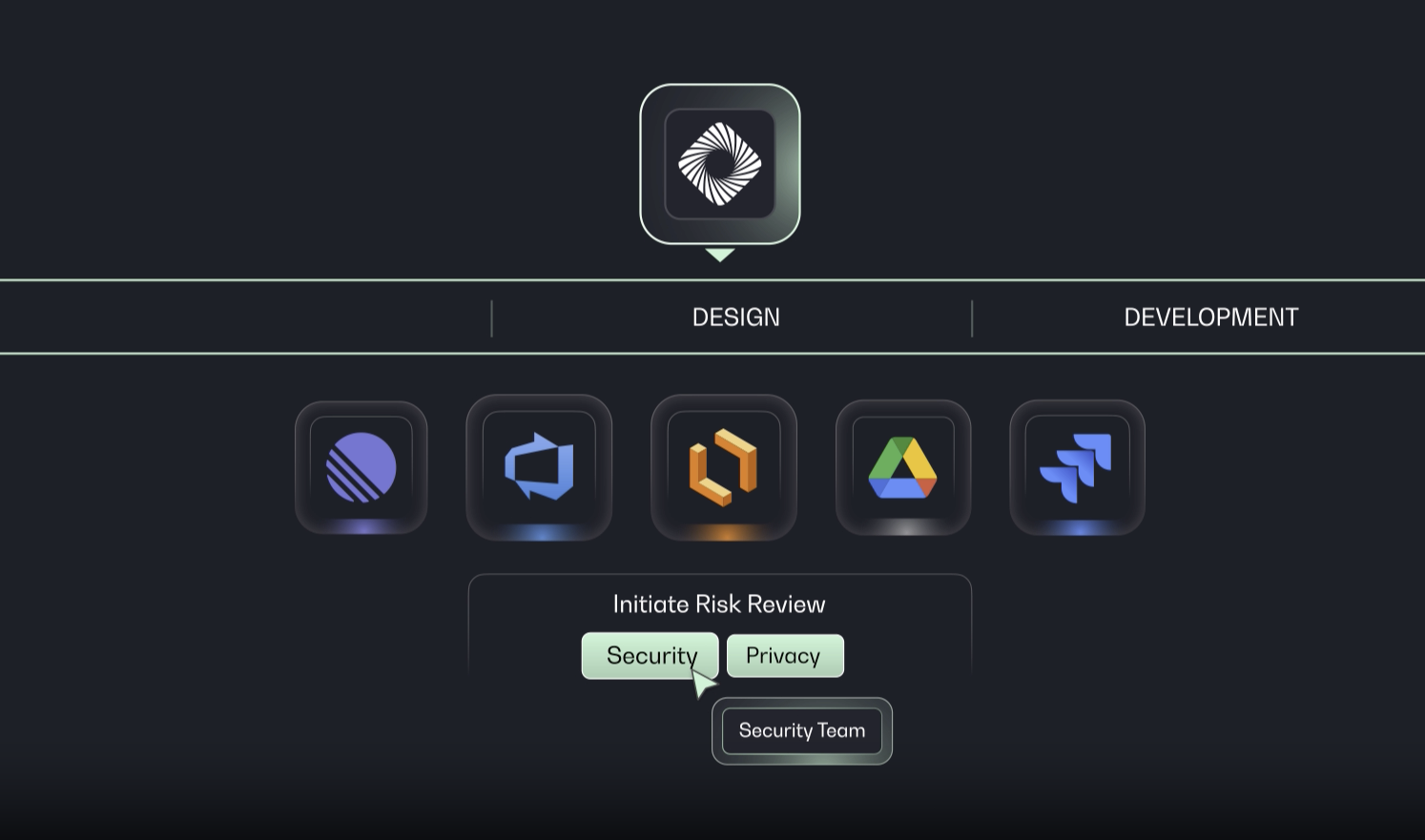
Proactively identify design flaws across all development work
Prime continuously scans all planned development work to proactively identify design flaws before code is written, expanding ProdSec team coverage, eliminating painful engineering rework, and strengthening the organization’s risk posture.
Customer Stories
FAQ
Prime integrates with leading engineering design and planning tools, including Jira, Confluence, Google Drive, Azure DevOps, Linear, and Git Issues. We’re continuously expanding our integrations. Reach out if you need support for a specific tool.
No, Prime empowers Product Security Engineers and Security Architects. Prime helps scale the team by automatically monitoring all engineering tasks and removes manual and tedious work from their day-to-day so the experts can focus on high-value tasks.
Yes! While some Jira tickets might be poorly written, Prime uses relationships in Jira, historical data, and additional data sources to enrich every task and understand the risk associated with it.
Prime conducts multiple iterations of every risk assessment to identify anomalies and errors with the internal analysis. Internal quality benchmarks are further used to control the quality and accuracy of presented results.
Prime doesn’t train models or sell customer data. All customer data is stored in a customer-dedicated AWS tenant. Customers can purge all or partial data upon request.
As a cybersecurity company, security is top of mind for us. Prime is SOC2 Type II certified to ensure that we build the most secure software for our customers.
Similarly to Threat Modeling, Prime focuses on the Design and Planning stages of the PDLC. However, we don’t believe that to assess risk engineers and security teams have to create complex diagrams. Prime utilizes available data and metadata to assess risk for each engineering task and plan. In some cases, this process might replace threat modeling, however, this is dependent on each company’s preferences.

.png)

.png)
.png)